The Access Control Tab
Access control is another feature which will, in theory,
reduce the chances of uninvited guests on your wireless network.
Access Control is another means of keeping casual hackers out of your network. It works by only allowing machines you explicitly specify to connect to your base station. By default, this feature is turned off.
The way that you specify what machine may connect is the so-called MAC address. In theory, there is a unique MAC address for every network device out there, be it ethernet, wireless, etc. Typically, the MAC address will be printed on the device or you can discover it via software.
For example, on base stations, the MAC addresses can be found printed on the underside. On Apple laptops that come with pre-installed internal Airport network cards, Apple typically prints the information inside the battery compartment. However, fear not! The Airport application in OS 9 or the Network Control Panel in OS X also give you that information, so no need to despair!
The MAC address can be identified by a series of hexadecimal numbers that are grouped in two's... Something like 00:30:AB:0A:89:01. In the OS 9 Airport Application, the number is displayed at the bottom of the window. In OS X, open the Network control panel, click on the Airport Tab, and look for the "Airport ID" at the bottom of the TCP/IP page.
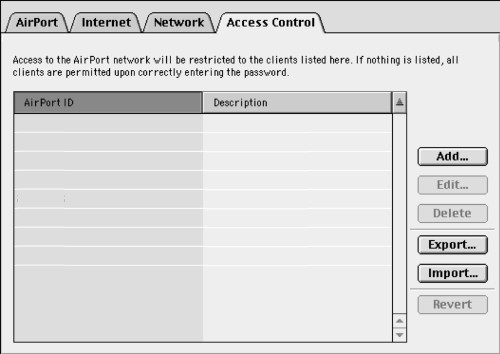
Now that you know how to find the MAC address, here is how you tighten security a little bit with Access Control: First, compile a list of MAC Addresses/Airport IDs you want to allow to access your network. Thankfully, Apple also allows you to assign a name for each access point. Thus, you can sort and identify MAC addresses not only by the hexadecimal number combination but by the name of the user.
Then, enter all the information into this panel using the "Add" button. Note however, that every user will now be required to be listed here or they won't be able to connect. That is, everyone who is not on the list is automatically disallowed.
For network administrators, Apple added a neat feature, whereby they can save all the Access Control data and then "Import" it into all the machines on their network. That way, they only have to enter the data once.
Before we start singing the praises of the enhanced security through Access Control, remember that the "protection" it affords will only keep out casual hackers. MAC adresses are sent in the clear, so all a hacker has to do is "sniff" the passing wirless traffic to see which MAC addresses are allowed, then change the MAC address his/her transmitter through a process called "spoofing", followed by masquerading into your network. Thus, access control is pretty useless in the face of determined hackers, sorry!
Click here for Apple's article on Access Control
You can now hit the "Update" button, watch the ABS status lights do their dance, and start enjoying your ABS. Just don't interrupt it while it is updating its settings or starting back up. Otherwise, you risk creating a paperweight. Cheers!
Constantin

